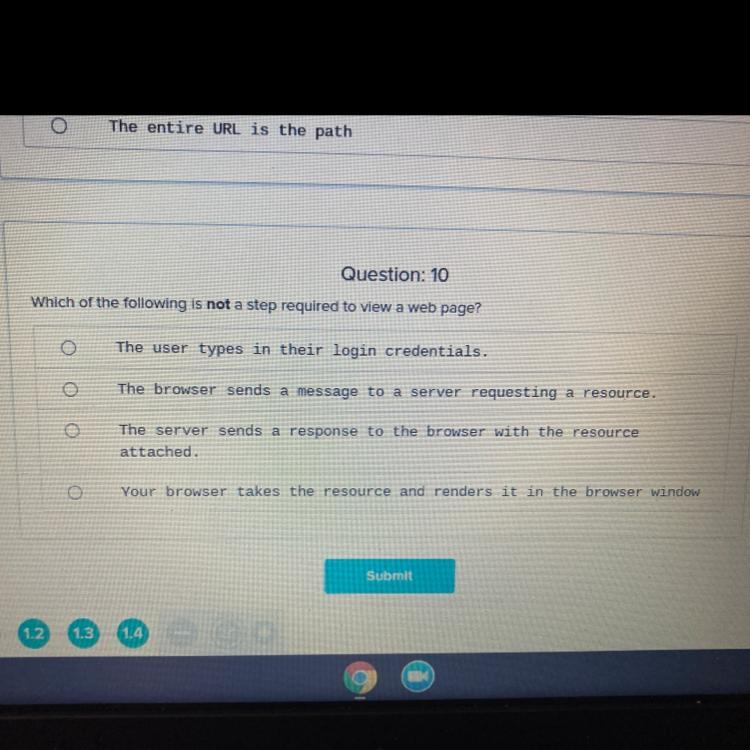
pls help!! which of the following is not a step required to view a web page?
Answers
Related Questions
an option already selected by windows is called____ ( default option/ default selection).
this is urgent
Answers
Answer:
default option
Explanation:
PLEASE HELP! Please dont answer if your going to guess
You have three modes for opening a file. You wish to create a new file and write data to
the file. What letter belongs in this line of code?
myFile = open("another.txt", "_____")
r
w
a
d
Answers
Answer:
r
Explanation:
I literally learned this today when trying to make a python server with an html file:)
Answer:
w
Explanation:
write examples of hacking in internet?
Answers
Answer:
Although hacking is very bad, it can be found everywhere and anywhere.
Examples: Phishing, password checking, and keyloggers
Explanation:
Explanation:
Hacking is an attempt to exploit a computer system or a private network inside a computer. Simply put, it is the unauthorised access to or control over computer network security systems for some illicit purpose.
To better describe hacking, one needs to first understand hackers. One can easily assume them to be intelligent and highly skilled in computers. In fact, breaking a security system requires more intelligence and expertise than actually creating one. There are no hard and fast rules whereby we can categorize hackers into neat compartments. However, in general computer parlance, we call them white hats, black hats and grey hats. White hat professionals hack to check their own security systems to make it more hack-proof. In most cases, they are part of the same organisation. Black hat hackers hack to take control over the system for personal gains. They can destroy, steal or even prevent authorized users from accessing the system. They do this by finding loopholes and weaknesses in the system. Some computer experts call them crackers instead of hackers. Grey hat hackers comprise curious people who have just about enough computer language skills to enable them to hack a system to locate potential loopholes in the network security system. Grey hats differ from black hats in the sense that the former notify the admin of the network system about the weaknesses discovered in the system, whereas the latter is only looking for personal gains. All kinds of hacking are considered illegal barring the work done by white hat hackers.
Define the term, external hard drive. Explain why you would use an external hard drive instead of a second internal hard drive.
Answers
Answer:
An external hard drive is a storage device located outside of a computer that is connected through a USB cable or wireless connection. An external hard drive is usually used to store media that a user needs to be portable, for backups, and when the internal drive of the computer is already at its full memory capacity.
Explanation:
External hard drives are usually portable thats why it is commonly used!
What is the correct HTML for adding a background color?
Question 7 options:
< background>yellow
< body background-color=yellow>
< body bg="yellow">
< body style="background-color:yellow;">
Answers
Answer:
< body background-color=yellow>
Explanation:
This is the correct HTML command that is used for adding a background color of choice.
first calculating device
Answers
Answer:
abacus is first calculating device
Define self-esteem: A how I feel about myself B how I visualize myself C how I esteem myself
Answers
Answer:
A how I feel about myself
Explanation:
Self-esteem is your overall opinion of yourself — how you feel about your abilities and limitations. When you have healthy self-esteem, you feel good about yourself and see yourself as deserving the respect of others. When you have low self-esteem, you put little value on your opinions and ideas.
4. Which of the following is a face-to-face meeting between the hiring party and the applicant?
A. Interview
B. Application
C. Résumé
D. Reference
Answers
Answer:
A. interview
Explanation:
You defined a class as follows.
def __init__(self, style, color):
self.style = style
self.color = color
This portion is the _____.
creator
instantiator
constructor
initiator
Answers
Answer:
instantiator
Explanation:
MRK ME BRAINLIEST PLZZZZZZZZZZZZZZZ
Answer:
instantiator
Explanation:
Plz help:(!!!!
Type the correct answer in the box. Spell all words correctly.
Claire wants to use a filter to ensure quality in the software development process and product. What can Claire use for this purpose?
Claire should use_________
as a filter to ensure quality in the software development process and product.
Answers
Answer:
Defect filters
Explanation:
Answer:
"a quality gate" is the correct answer :D
Explanation:
Match each storyboarding technique with its appropriate description.
Answers
Answer:
Hierarchical – Option C
Linear – Option D
Webbed - Option A
Wheel - Option B
Explanation:
Hierarchical means something that follows the order from general to specific .
Hierarchical – Option C
Linear means something that follows the order from general to specific .
Linear – Option D
Webbed – There is no order in flow of information or it is inconsequential. Hence, option A
Wheel - means the flow is sequential i.e as per the sequence
Wheel – Option B
What browser do you use?
Brave
Chrome
Firefox
Opera
Edge
Tor
Answers
Answer:
Explanation:
one day when rahul went to his computer lab and saw that all the computers were connected to a single printer and whoever is giving a command to print, the print out comes from that printer. can you name the concept of communication? class 8 computer one word answer..
Answers
Explanation:
you can connect multiple PCs to the wireless printer and print your documents from each one of them as long as the printer can be connected to the same network . You need the disc that came with the wireless printer to install the correct drivers on your computers and laptops.
hope it helps ( brainleist please )
Consider the following code.
public void printNumbers(int x, int y) {
if (x < 5) {
System.out.println("x: " + x);
}
if (y > 5) {
System.out.println("y: " + y);
}
int a = (int)(Math.random() * 10);
int b = (int)(Math.random() * 10);
if (x != y) printNumbers(a, b);
}
Which of the following conditions will cause recursion to stop with certainty?
A. x < 5
B. x < 5 or y > 5
C. x != y
D. x == y
Consider the following code.
public static int recur3(int n) {
if (n == 0) return 0;
if (n == 1) return 1;
if (n == 2) return 2;
return recur3(n - 1) + recur3(n - 2) + recur3(n - 3);
}
What value would be returned if this method were called and passed a value of 5?
A. 3
B. 9
C. 11
D. 16
Which of the following methods correctly calculates the value of a number x raised to the power of n using recursion?
A.
public static int pow(int x, int n) {
if (x == 0) return 1;
return x * pow(x, n);
}
B.
public static int pow(int x, int n) {
if (x == 0) return 1;
return x * pow(x, n - 1);
}
C.
public static int pow(int x, int n) {
if (n == 0) return 1;
return x * pow(x, n);
}
D.
public static int pow(int x, int n) {
if (n == 0) return 1;
return x * pow(x, n - 1);
}
Which of the following methods correctly calculates and returns the sum of all the digits in an integer using recursion?
A.
public int addDigits(int a) {
if (a == 0) return 0;
return a % 10 + addDigits(a / 10);
}
B.
public int addDigits(int a) {
if (a == 0) return 0;
return a / 10 + addDigits(a % 10);
}
C.
public int addDigits(int a) {
return a % 10 + addDigits(a / 10);
}
D.
public int addDigits(int a) {
return a / 10 + addDigits(a % 10);}
The intent of the following method is to find and return the index of the first ‘x’ character in a string. If this character is not found, -1 is returned.
public int findX(String s) {
return findX(s, 0);
}
Which of the following methods would make the best recursive helper method for this task?
A.
private int findX(String s) {
if (index >= s.length()) return -1;
else if (s.charAt(index) == 'x') return index;
else return findX(s);
}
B.
private int findX(String s, int index) {
if (index >= s.length()) return -1;
else return s.charAt(index);
}
C.
private int findX(String s, int index) {
if (index >= s.length()) return -1;
else if (s.charAt(index) == 'x') return index;
else return findX(s, index);
}
D.
private int findX(String s, int index) {
if (index >= s.length()) return -1;
else if (s.charAt(index) == 'x') return index;
else return findX(s, index + 1);
}
Answers
Is this for a grade?
What form of infrastructure improved trade and communication among Roman cities?
aqueducts
canals
reservoirs
roads
Answers
Answer:
aqueducts
Explanation:
Answer:
c
Explanation:
A small computer on a smart card has 4 page frames. At the first clock tick, the R bits are 1000 (page 0 is 1 and the rest are 0). At subsequent ticks, the values are 0110, 0101, 1010, 1101, 0101, 0011, and 1100. If the aging algorithm is used with a 16-bit counter, give the values of the four counters after the last tick. If page fault occurs, which page should be swapped out
Answers
Answer and Explanation:
Aging algorithm Aging algorithms are the NFU algorithm with modification to know the time of span and increment the page referenced. The ageing method sort customer invoices by date in four columns. By using the ageing algorithm, counters are shifted by 1 bit, and the R bit is added to the leftmost bit. The values of counters are
Page 0: 01101110
Page 1: 01001001
Page 2: 00110111
Page 3: 10001011
The system clock is 2ns and interval is 2ms for that one bit per interval is the ability to analyze the references in a tick. Counters have a finite number and have two pages, where counter value 0 have two pages. The page fault appears, and pick just one of them randomly.
What are good components to preorder a PC with that are cheep? It would be my first PC by the way.
Answers
Answer:
Good Components
.CPU AMD Threadripper 3960X Amazon
.CPU cooler NZXT Kraken X63 (280mm AIO liquid cooler) Overclockers
.GPU Zotac Gaming GeForce GTX 1660 6GB CCLonline
.Memory 32GB Corsair Dominator Platinum RGB 3200MHz Scan
Explanation:
Engineers at Edison Laboratories developed a _____ strip that allowed them to capture sequences of images on film.
kinetoscope
selenium
cotton
celluloid
Answers
Answer:
Celluloid
Explanation:
It is Sis
Which of the following images illustrates safe driving?
Answers
Answer:
bottom left
Explanation:
Answer:
keep your eyes on the road!!!!
What is the output of this program?
grades = [89, 70, 98, 100, 83]
print(grades[-4])
Group of answer choices
89
100
70
98
Answers
Answer:
70 is the answer negative one begins from 83 and count down to 89, Therefore, 70 is is -4 and is chosen as the best answer
Type the correct answer in the box. Spell all words correctly.
The students of a college have to create their assignment reports using a word processing program. Some of the questions in their assignment involve comparison between different items. Which function of a word processing program will be the most useful to present this information?
The function of a word processing program will be the most useful for comparison.
Answers
Answer:
The Insert Table function
Explanation:
Presenting information that involves the comparison between different (two or more) items where the given details on the items are available as text will be aided when the similarities and differences of the information are placed side by side, such as in tabular form categorically arranged with rows listing items under comparison
The function in a word processing program such as MS Word that would be most useful, therefore, is the Insert Table function
The Insert Table function is located under the Insert menu on the Menu bar, where the table, in the drop down list under the Table button
When the Table drop-down button is clicked, it reveals a table that can be adjusted to different number of columns and rows by moving the mouse.
After the table with the desired number of columns and rows is inserted, the comparison between specific characteristics of the items in the assignment report can then be placed in different columns on the same row in the created table.
Answer:
The insert table function of a word processing program will be the most useful for comparison.
Explanation:
Readable code includes the use of
color and symbols to make the code look good.
consistent and meaningful variable names, helpful comments, and formatting.
variable names that do not vary from program to program.
comments that include the programmers' reactions to a particular piece of code used.
Answers
Answer:
bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBbBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBbbbbbbbbbbbbbbbbbbbbbbbbBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB
Explanation:
The Readable code includes the use of color and symbols to make the code look good is; A consistent and meaningful variable names, helpful comments, and formatting.
Since Readable code is crucial for software development. It makes it easier for programmers to understand, modify, and maintain the code. It is well-organized, with consistent and meaningful variable names, helpful comments, and proper formatting.
Using consistent and meaningful variable names allows programmers to easily understand what the variable represents.
Helpful comments also play a crucial role in making the code readable. Comments should be used to explain, the code is doing, why it is doing it, and any other important details that would help programmers understand the code.
Formatting is also essential in making the code readable.
In summary, readable code includes consistent and meaningful variable names, helpful comments, and proper formatting.
Learn more about the code here;
https://brainly.com/question/14278291
#SPJ4
Rob is planning his housewarming party. He wants to design an invitation and personalize it for each invitee. He needs to create a list of invitees, design the card, and personalize the card. How should he complete the tasks? a. Use mail merge for steps 1 and 2 and a word processor for step 3. b. Use a graphics software for step 1, mail merge for step 2, and a word processor for step 3. c. Use a word processor for steps 1 and 2 and a graphics software for step 3. d. Use a word processor for step 1, graphics software for step 2, and a mail merge for step 3.
Answers
Answer:
1: Word Processor
2: Graphics Software
3: Mail Merge
Explanation:
Given
1. Create a list of invitees
2. Design an invitation card
3. Personalize the card
Creating a list of invitees is a task that requires basic activities such as typing, using of numbers and bullets; these activities can be achieved using word processing software programs such as Microsoft Word, WordPerfect, amongst others.
So task 1 requires a word processor
An invitation card is a piece of graphics that can be perfectly handled by graphics software programs such as CorelDraw, Adobe Photoshop, etc.
So task 1 requires a graphics software
Task 3 can be achieved using mail merge and this is because mail merge can be used either to print or to mail recipients. While mailing the recipients, one can easily personalize each letter (or in this case, an invitation card) to suit the recipient it is being directed to.
You are planning a storage solution for a new Windows server. The server will be used for file and print services and as a database server. The new server has five hard disks, all with equal capacity. Your storage solution should meet the following requirements: System files should be on a volume separate from data files. All volumes should be protected so that the server can continue to run in the event of a failure of one of the disks. The data volume should be optimized for improved disk access times. You will use Windows Disk Management to create and manage the volumes. What should you do
Answers
Answer:
Explanation:
The best solution for this scenario would be to first create a mirrored volume for the system volume using two of the available disks and then a single RAID 5 volume with the remaining 3 disks for the data volume. This setup will allow all of the data to be backed up so that if one of the disks fails the server will continue running accordingly. The RAID 5 volume offers error checking and redundancy for the data, therefore, allowing the data to be accessed quickly and efficiently with far greater security and far less chance of data becoming corrupt.
Which file organisation has the quickest access to data files? *
1 point
a)Direct
b)Serial
c)Sequential
d)Transaction
Answers
Functions of file in computer
Answers
[tex]\huge{\textbf{\textsf{{\color{pink}{An}}{\red{sw}}{\orange{er}} {\color{yellow}{:}}}}}[/tex]
File in computers are used to store data, information and commands.
Thanks hope it helps.Pls mark as brainliest.Telecommunications, outsourcing, flextime, teamwork, and diversity are workplace trends adopted to
O True
O False
Answers
Answer:
False
Explanation:
Outsourcing and telecommuting are the trends related to presence of growing technology within the economy allowing various services to be outsourced to people who are more of an expert when it comes to handling those procedures.
(WEB DESIGN FINAL QUESTION) PLEASE HELP
what is a trademark?
Answers
Answer:
a trade mark is something where someone owns the rights to something in a specific country
Irene is creating a wireframe of a website she is working on to show her client. In which phase of the development process is she?
A. planning
B. design
C. development
D. testing
Answers
Answer:
The Answer Is B: Design
Explanation:
I took the test on edmentum and it was correct your welcome m8 :)
Which of the following code snippets will output the following:
Hello
Hello
Hello
A:
print("Hello")
print("Hello")
print("Hello")
B:
for i in range(3):
print("Hello")
C:
print("Hello"*3)
D:
print("Hello\n"*3)
Answers
Answer:
A, B and D
Explanation:
Given
Options (a) to (d)
Required
Which outputs
Hello
Hello
Hello
(a) Each print statement prints "Hello" on separate lines.
Since there are three print statements, then (a) is true
(b) The loop iterates 3 times; and each iteration prints "Hello" on separate line,
Hence, (b) is also true
(c) The statement prints "Hello" 3 times, but all are on the same line
Hence, (c) is false
(d) The statement prints "Hello" 3 times; The '\n' ensures that each "Hello" string is printed on separate line.
Hence, (d) is true
Answer:
option A B D
Explanation:
hope helps you
have a nice day