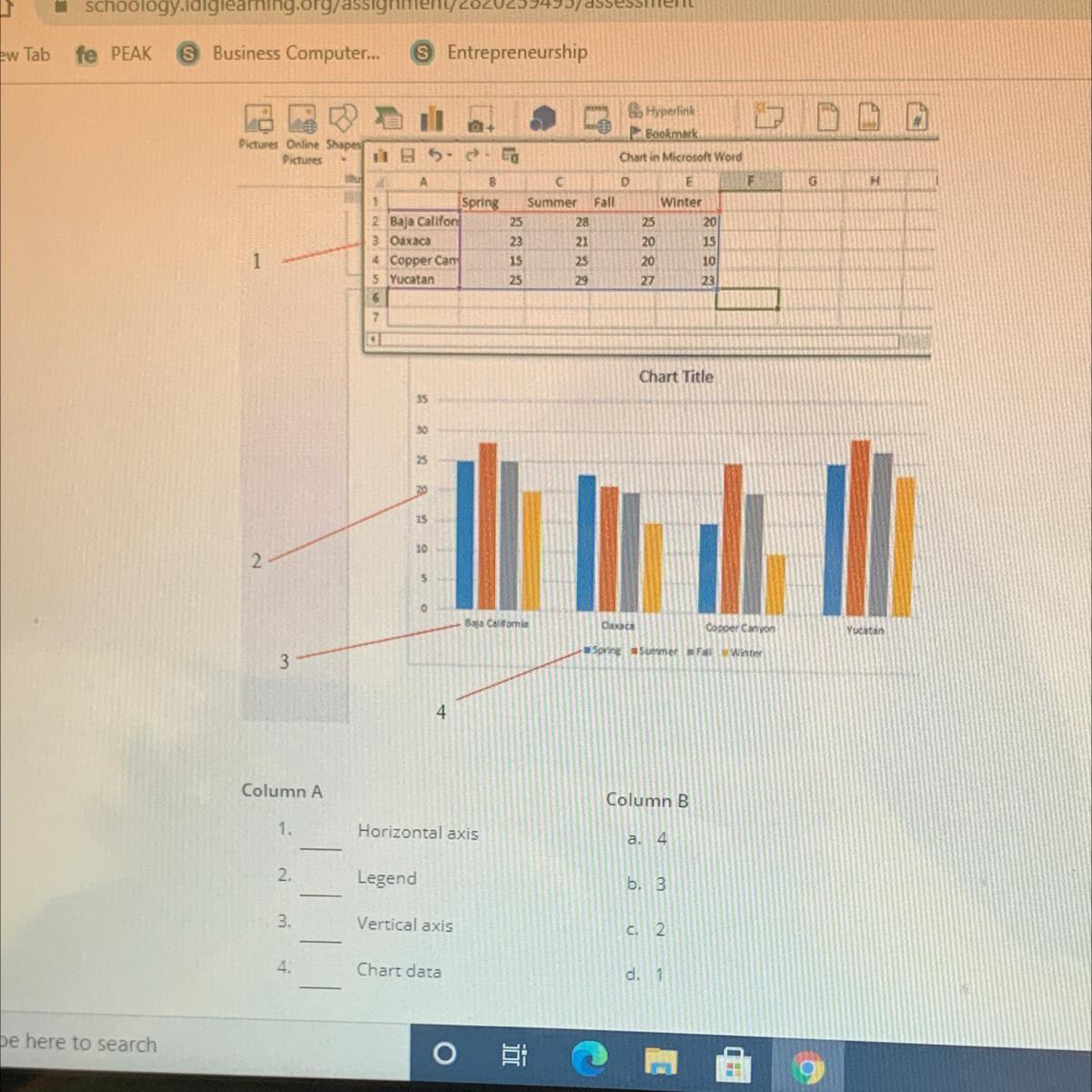
Match letters from column B to Column A by looking at the picture above.
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
This question is about mapping correct terms with their number in the given picture. The correct matching of Column A and Column B is given below
Column A Column B
Horizontal axis 3
Legend 4
Vertical axis 2
Chart Data 1
Related Questions
In a system where Round Robin is used for CPU scheduling, the following is TRUE when a process cannot finish its computation during its current time quantum? The process will terminate itself. The process will be terminated by the operating system. The process's state will be changed from running to blocked. None of the mentioned.
Answers
Answer:
B. The process will be terminated by the operating system.
Explanation:
When Round Robin is used for CPU scheduling, a time scheduler which is a component of the operating system is used in regulating the operation. A time limit is set for each of the processes to be run.
So, when a process fails to complete running before its time elapses, the time scheduler would log it off and return it to the queue. This queue is in a circular form and gives each of the processes a chance to run its course.
Based on the information given regarding CPU scheduling, the correct option is C. The process's state will be changed from running to blocked.
It should be noted that in a system where Round Robin is used for CPU scheduling, when a process cannot finish its computation during its current time quantum, the process's state will be changed from running to blocked.
It should be noted that a prices transition to a blocked state occurs when it's waiting for some events like a particular resource becoming available.
Learn more about CPU scheduling on:
https://brainly.com/question/19999569
In Python
Write the special method __str__() for CarRecord.
Sample output with input: 2009 'ABC321'
Year: 2009, VIN: ABC321
Answers
Answer:
def __str__(self):
return ('Year: %d, VIN: %s' %(self.year_made, self.car_vin))
Explanation:
Here you go! This should do it.
The program gives an implementation of the car record class which displays the model year and registration number of a car. The program written in python 3 goes thus :
class CarRecord :
#initialize a class named carRecord
def __init__(self):
#define the init method of the class
self.year_made = 0
#year car was made is initialized to 0 (integer)
self.car_vin = ' '
#vehicle registration is an empty string
def __str__(self):
#define an str method
return f"Year:{self.year_made}, VIN:{self.car_vin}"
#returns formatted display of the year and VIN number
my_car = CarRecord()
#creates an instance of the carRecord class
my_car.year_made = int(input())
#prompts user for the model year of the car
my_car.car_vin = input()
#prompts user for the model Vin number
print(my_car)
# display the details
A sample run of the program is given
Learn more :https://brainly.com/question/20504501
A country, called Simpleland, has a language with a small vocabulary of just “the”, “on”, “and”, “go”, “round”, “bus”, and “wheels”. For a word count vector with indices ordered as the words appear above, what is the word count vector for a document that simply says “the wheels on the bus go round and round.”
Please enter the vector of counts as follows: If the counts were ["the"=1, “on”=3, "and"=2, "go"=1, "round"=2, "bus"=1, "wheels"=1], enter 1321211.
1 point
Answers
Answer:
umm that is a todler song
Explanation:
umm that is a todler song that they sing to them when there crying
A country, called Simpleland, has a language with a small vocabulary of just “the”, “on”, “and”, “go”, “round”, “bus”, and “wheels”. As per the given scenario, the vector of counts will be 2111211. The correct option is C.
What are the ways to count items in a vector?C++ has a built-in function that counts the length of the vector. Size is the function's name ().
It returns the size or total number of elements of the vector that was utilized to create it. There is no need for debate.
The number of observations (rows) includes deleted observations as well. In an SAS data collection, there can be a maximum of 2 63-1 observations, or roughly 9.2 quintillion observations. For the majority of users, going above that limit is quite rare.
The vector of counts in the above scenario will be 2111211.
Thus, the correct option is C.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ2
what is scientific and
Answers
Answer:
And what??????????????
what is Service Operations in ITIL
Answers
Explanation:
the objective of ITIL service operations is to make sure that IT services are delivered effectively and efficiently. the service operation life cycle stage includes the fulfilling of user requests, resolving service failure fixing problems and also carrying out routine operational tasks
A have a string, called "joshs_diary", that is huge (there was a lot of drama in middle school). But I don't want every one to know that this string is my diary. However, I also don't want to make copies of it (because my computer doesn't have enough memory). Which of the following lines will let me access this string via a new name, but without making any copies?
a. std::string book = joshs_diary;
b. std::string & book = joshs_diary; const
c. std::string * book = &joshs_diary;
d. std::string book(joshs_diary);
e. const std::string & book = joshs_diary;
f. const std::string * const book = &joshs_diary;
g. std::string * book = &joshs_diary;
Answers
Answer:
C and G
Explanation:
In C language, the asterisks, ' * ', and the ampersand, ' & ', are used to create pointers and references to pointers respectively. The asterisks are used with unique identifiers to declare a pointer to a variable location in memory, while the ampersand is always placed before a variable name as an r_value to the pointer declared.
Please help me. Anyone who gives ridiculous answers for points will be reported.
Answers
Answer:
Well, First of all, use Linear
Explanation:
My sis always tries to explain it to me even though I know already, I can get her to give you so much explanations XD
I have the Longest explanation possible but it won't let me say it after 20 min of writing
A____server translates back and forth between domain names and IP addresses.
O wWeb
O email
O mesh
O DNS
Answers
Answer:
DNS
Explanation:
Hope this helps
Jake or Peggy Zale must fix quickly the fax.
Answers
Answer:
Sentence: Jack or Peggy Zale must fix quickly the fax.
Correct: Either Jack or Peggy Zale must quickly fix the fax.
There are 2 errors in these sentence construction. In stating two persons as an option we must use the word "either" to indicate that you only have two choose from the two of them. The word "
Explanation:
The correct sentence would be "either Jake or Peggy Zale must quickly fix the fax".
In the question construction, there is a conjunction and misarrangement error.
In conclusion, the word " "either Jake or Peggy Zale must quickly fix the fax" is correct
Read more about conjunction
brainly.com/question/8094735
Secondary sources
information gathered from primary sources.
Answers
Answer:
The answer is interpret Proof is down below
Explanation:
Here is the proooooooffffffff i made a 90 but this one was right
Secondary sources interpret information gathered from primary sources.
What are Secondary sources of information?A secondary source is known to be made up of discussion that is often based on a primary information source.
Hence, the feature of secondary sources are known to give some kind of interpretation to all the information that has been gathered from other primary sources.
Learn more about Secondary sources from
https://brainly.com/question/896456
#SPJ2
Write a C program to input basic salary of an employee and calculate gross salary according to given conditions.
Basic Salary <= 10000 : HRA = 20%, DA = 80%
Basic Salary is between 10001 to 20000 : HRA = 25%, DA = 90%
Basic Salary >= 20001 : HRA = 30%, DA = 95%
Your program must calculate each employee's gross pay amount.
Answers
Answer:
Written in C
#include <stdio.h>
int main() {
float salary;
printf("Salary: ");
scanf("%f", &salary);
float HRA, DA;
if(salary <= 10000){
HRA = 0.20; DA = 0.80;
}
else if(salary >= 10000 && salary <= 20000){
HRA = 0.25; DA = 0.90;
}
else{
HRA = 0.30; DA = 0.95;
}
salary = salary + salary * HRA + salary * DA;
printf("Gross Salary: %.2f\n", salary);
return 0;
}
Explanation:
I've added the full program as an attachment where I used comments as explanation
4.3 Code Practice: Question 2
Write a program that uses a while loop to calculate and print the multiples of 3 from 3 to 21. Your program should print each number on a separate line.
(Python)
Answers
i = 3
while i <= 21:
if i % 3 == 0:
print(i)
i += 1
The required program written in python 3 is as follows :
num = 3
#initialize a variable called num to 3
multiples_of_3 = []
#empty list to store all multiples of 3
while num <=21 :
#while loop checks that the range is not exceeded.
if num%3 == 0:
#multiples of 3 have a remainder of 0, when divided by 3.
multiples_of_3.append(num)
#if the number has a remainder of 0, then add the number of the list of multiples
num+=1
#add 1 to proceed to check the next number
print(multiples_of_3)
#print the list
Learn more :https://brainly.com/question/24782250
Suppose one machine, A, executes a program with an average CPI of 1.9. Suppose another machine, B (with the same instruction set and an enhanced compiler), executes the same program with 20% less instructions and with a CPI of 1.1 at 800MHz. In order for the two machines to have the same performance, what does the clock rate of the first machine need to be
Answers
Answer:
the clock rate of the first machine need to be 1.7 GHz
Explanation:
Given:
CPI of A = 1.9
CPI of B = 1.1
machine, B executes the same program with 20% less instructions and with a CPI of 1.1 at 800MHz
To find:
In order for the two machines to have the same performance, what does the clock rate of the first machine need to be
Solution:
CPU execution time = Instruction Count * Cycles per Instruction/ clock rate
CPU execution time = (IC * CPI) / clock rate
(IC * CPI) (A) / clock rate(A) = (IC * CPI)B / clock rate(B)
(IC * 1.9) (A) / clock rate(A) = (IC * (1.1 * (1.0 - 0.20)))(B) / 800 * 10⁶ (B)
Notice that 0.20 is basically from 20% less instructions
(IC * 1.9) / clock rate = (IC * (1.1 * (1.0 - 0.20))) / 800 * 10⁶
(IC * 1.9) / clock rate = (IC*(1.1 * ( 0.8))/800 * 10⁶
(IC * 1.9) / clock rate = (IC * 0.88) / 800 * 10⁶
clock rate (A) = (IC * 1.9) / (IC * 0.88) / 800 * 10⁶
clock rate (A) = (IC * 1.9) (800 * 10⁶) / (IC * 0.88)
clock rate (A) = 1.9(800)(1000000) / 0.88
clock rate (A) = (1.9)(800000000) / 0.88
clock rate (A) = 1520000000 / 0.88
clock rate (A) = 1727272727.272727
clock rate (A) = 1.7 GHz
1. When you write HTML code, you use ______ to describe the structure of information on a webpage. a. a web address b. tags c. styles d. links
Answers
Answer:
b. tags
Explanation:
When you write HTML code, you use tags to describe the structure of information on a webpage. These tags are represented by the following symbols <>. All of HTML is written using different types of tags such as <body>, <main>, <div>, <nav>, etc. Each of these serves a different purpose but are all used for structuring the specific information on a website so that the information is well organized and is not all on top of each other. This also allows for specific sections to be easily targeted and styles separately from the other sections.
describe how to get started on a formal business document by using word processing software
Answers
Answer:Click the Microsoft Office button.
Select New. The New Document dialog box appears.
Select Blank document under the Blank and recent section. It will be highlighted by default.
Click Create. A new blank document appears in the Word window.
Explanation:
The Gas-N-Clean Service Station sells gasoline and has a car wash. Fees for the car wash are $1.25 with a gasoline purchase of $10.00 or more and $3.00 otherwise. Three kinds of gasoline are available: regular at $2.89, plus at $3.09, and super at $3.39 per gallon. User Request:
Write a program that prints a statement for a customer. Analysis:
Input consists of number of gallons purchased (R, P, S, or N for no purchase), and car wash desired (Y or N). Gasoline price should be program defined constant. Sample output for these data is
Enter number of gallons and press 9.7
Enter gas type (R, P, S, or N) and press R
Enter Y or N for car wash and press Y
**************************************
* *
* *
* Gas-N-Clean Service Station *
* *
* March 2, 2004 *
* * ************************************** Amount Gasoline purchases 9.7 Gallons Price pre gallons $ 2.89 Total gasoline cost $ 28.03 Car wash cost $ 1.25 Total due $ 29.28 Thank you for stopping Pleas come again Remember to buckle up and drive safely
Answers
Answer:
import java.util.Scanner;
public class Main
{
public static void main(String[] args) {
//print the header
System.out.println("**************************************");
System.out.println("* *");
System.out.println("* *");
System.out.println("* Gas-N-Clean Service Station *");
System.out.println("* *");
System.out.println("* March 2, 2004 *");
System.out.println("* *");
System.out.println("**************************************");
//set the constant values for gasoline
final double REGULAR_GASOLINE = 2.89;
final double PLUS_GASOLINE = 3.09;
final double SUPER_GASOLINE = 3.39;
// initialize the variables as 0
double gasolinePrice = 0, gasolineCost = 0, carWashCost = 0, totalCost = 0;
Scanner input = new Scanner(System.in);
//ask the user to enter the gallons, gas type and car wash choice
System.out.print("Enter number of gallons ");
double gasolinePurchase = input.nextDouble();
System.out.print("Enter gas type (R, P, S, or N) ");
char gasType = input.next().charAt(0);
System.out.print("Enter Y or N for car wash ");
char carWashChoice = input.next().charAt(0);
//check the gas type. Depending on the choice set the gasolinePrice from the corresponding constant value
if(gasType == 'R')
gasolinePrice = REGULAR_GASOLINE;
else if(gasType == 'P')
gasolinePrice = PLUS_GASOLINE;
else if(gasType == 'S')
gasolinePrice = SUPER_GASOLINE;
//calculate the gasolineCost
gasolineCost = gasolinePurchase * gasolinePrice;
//check the carWashChoice. If it is yes and gasolineCost is greater than 10, set the carWashCost as 1.25. Otherwise, set the carWashCost as 3.00
if(carWashChoice == 'Y'){
if(gasolineCost >= 10)
carWashCost = 1.25;
else
carWashCost = 3.00;
}
//calculate the total cost, add gasolineCost and carWashCost
totalCost = gasolineCost + carWashCost;
//print the values in required format
System.out.println("Amount Gasoline purchases " + gasolinePurchase);
System.out.println("Gallons Price per gallons $ " + gasolinePrice);
System.out.printf("Total gasoline cost $ %.2f\n", gasolineCost);
System.out.println("Car wash cost $ " + carWashCost);
System.out.printf("Total due $ %.2f\n", totalCost);
System.out.println("Thank you for stopping\nPlease come again \nRemember to buckle up and drive safely");
}
}
Explanation:
*The code is in Java.
Please see the comments in the code for explanation
How does asymmetric encryption work?
A.
It uses only one key to encrypt and decrypt a message.
B.
A private key is used to encrypt the message and the public key is used to decrypt the message.
C.
Either the public key or the private key can be used to encrypt and decrypt a message.
D.
Public key is used to encrypt the message and private key is used to decrypt the message.
Answers
Answer:
i choose choice D
Explanation:
reason as to my answer public keys are simply input keys used to encrypt data into either a computer or any electrical device as private keys are out put used to either erase or edit
1 megabyte is equal to 1024 gigabyte. True/False
Answers
Answer:
false
Explanation:
1 MB = 0.001 GB
If the propagation delay through a full-adder (FA) is 150 nsec, what is the total propagation delay in nsec of an 8-bit ripple-carry adder
Answers
Answer:
270 nsec
Explanation:
Ripple-carry adder is a combination of multiple full-adders. It is relatively slow as each full-adder waits for the output of a previous full-adder for its input.
Formula to calculate the delay of a ripple-carry adder is;
= 2( n + 1 ) x D
delay in a full-adder = 150 nsec.
number of full-adders = number of ripple-carry bits = 8
= 2 ( 8 + 1 ) x 150
= 18 x 150
= 270 nsec
The __________ list is intended to facilitate the development of the leading free network exploration tool.
Answers
Answer:
Nmap development list
Explanation:
The list being mentioned in this question is known as the Nmap development list. This list basically acts as an information gathering and analytical tool. It allows the user to easily roll out and integrate Nmap tools on a network in order to easily detect all of the IP addresses that are connected as well as analyze all of the details regarding each connected individual system. All of this information is highly valuable to a developer and facilitates the development process.
How can a LAN be changed into a WAN?
Answers
Answer:
I hope the above picture may help you.
(Sorry I just need these last points but I figured since probably no one else would answer that I could use these points so....sorry)
Java Eclipse Homework JoggerPro
Over a seven day period, a jogger wants to figure out the average number of miles she runs each day.
Use the following information to create the necessary code. You will need to use a loop in this code.
The following variables will need to be of type “double:”
miles, totalMiles, average
Show a title on the screen for the program.
Ask the user if they want to run the program.
If their answer is a capital or a lowercase letter ‘Y’, do the following:
Set totalMiles to 0.
Do seven times (for loop)
{
Show which day (number) you are on and ask for the number of miles for this day.
Add the miles to the total
}
Show the total number of miles
Calculate the average
Show the average mileage with decimals
Use attractive displays and good spacing.
Save your completed code according to your teacher’s directions.
Answers
import java.util.Scanner;
public class JoggerPro {
public static void main(String[] args) {
String days[] = {"Monday?", "Tuesday?", "Wednesday?", "Thursday?","Friday?","Saturday?","Sunday?"};
System.out.println("Welcome to JoggerPro!");
Scanner myObj = new Scanner(System.in);
System.out.println("Do you want to continue?");
String answer = myObj.nextLine();
if (answer.toLowerCase().equals("y")){
double totalMiles = 0;
for (int i =0; i < 7; i++){
System.out.println(" ");
System.out.println("How many miles did you jog on " + days[i]);
double miles = myObj.nextDouble();
totalMiles += miles;
}
double average = totalMiles / 7;
System.out.println(" ");
System.out.println("You ran a total of " + totalMiles+ " for the week.");
System.out.println(" ");
System.out.println("The average mileage is " + average);
}
}
}
I'm pretty sure this is what you're looking for. I hope this helps!
In 2-5 paragraphs, describe how technology helps business professionals to be more efficient.
Answers
The ways that technology helps business professionals to be more efficient is that Business professionals may stay more organized, communicate more effectively, and keep firms secure with the use of technology.
Technology makes it simpler to connect with employees by utilizing e-mail and memos, and it helps keep employee information and corporate paperwork a lot more organized using computers and software.
How does technology improve the productivity of business people?By streamlining time-consuming procedures, technology also increases office productivity. For instance, using document management software eliminates the need for manual data entry, filing, as well as in file retrieval.
Therefore, one can say that Technology can be used to safeguard private executive decisions, financial data, and other forms of proprietary information that gives a company a competitive edge. Simply simply, technology aids firms in protecting their ideas from rivals.
Learn more about technology from
https://brainly.com/question/1162014
#SPJ1
A pedometer treats walking 2,000 steps as walking 1 mile. Write a program whose input is the number of steps, and whose output is the miles walked. If the input is 5345, the output is 2.6725.
Answers
In python:
print(steps_walked / 2000)
Plz answer me will mark as brainliest
Answers
how many basic element makes up a computer system
Answers
Answer:
4
Explanation:
Input/output, datapath, control, and memory
There wrong its C bold it.
:)))))
Online Privacy
1.)Explain why is online privacy a controversial topic?
2.)Explain why this issue is applicable to you and your peers.
3.)Explain why this issue is a federal issue and not a state or local issue.
Answers
Answer:
Yes
Explanation:
Online privacy is a controversial topic due to the fact that it's a very hard thing to navigate. Some websites use cookies that are used to store your data so in a way there taking your privacy away which is controversial because of the way they use the information. Some websites store it for use of ads while others sell it. This issue is applicable to me and my peers because of the way we use technology. It can be used to steal my information about where I live and what I look up online. Also, the information stored could have my credit or debit card credentials. This issue should be a federal and nationwide issue because this is an everyday occurrence and leaves tons of people in crushing debt every year.
3.What are the pros and cons of using a linked implementation of a sparse matrix, as opposed to an array-based implementation
Answers
Answer:
speed and storage
Explanation:
The pros and cons of both are mainly in regards to speed and storage. Due to linked lists elements being connected to one another it requires that each previous element be accessed in order to arrive at a specific element. This makes it much slower than an array-based implementation where any element can be quickly accessed easily due to it having a specific location. This brings us to the other aspect which is memory. Since Arrays are saved as a single block, where each element has a specific location this takes much more space in the RAM as opposed to a linked implementation which is stored randomly and as indexes of the array itself.
Array Implementation:
Pros: Much Faster and Easier to target a specific elementCons: Much More Space neededLinked Implementation
Pros: Less overall space neededCons: Much slower speed.Which feature of a database allows a user to locate a specific record using keywords?
Chart
Filter
Search
Sort
Answers
Answer:
Search
Explanation:
Because you are searching up a specific recording using keywords.
I hope this helps
Answer:
Filter
Explanation:
I got it correct for a quiz.
How has the rise of mobile development and devices impacted the IT industry, IT professionals, and software development
Answers
Answer:
Throughout the interpretation section elsewhere here, the explanation of the problem is summarized.
Explanation:
The growth of smartphone production and smartphone apps and services, as well as the production of smartphones, has had a positive influence on the IT industry, IT practitioners, as well as the development of the technology. As normal, the primary focus is on smartphone apps instead of just desktop software. As we recognize, with innovative features, phone applications, and smartphones are all made, built, modernized every day, and always incorporated with either the latest technology.This has now resulted in far more jobs and employment for the IT sector, and therefore new clients for service-based businesses. It provided various-skilling the application production industry for IT experts including learning how to work on emerging technology. The demand for software production and software growth is evolving at a greater speed than it's ever been, so the increase of smartphone production and smartphones has had a very beneficial effect on perhaps the IT sector, IT practitioners, and business development.